How to Become a Spy

Spy Training Course
Have you ever wanted to become a spy? Well, if so there are a few things you need to learn.
Disguises and cover are essential. Being able to blend into a crowd is a key skill spies have to learn. Next, knowing the basic procedures (or "tradecraft") used by spies for things like communication will help prevent you from getting caught.
In addition, it's always nice to have an overview about how to get hired at an Intelligence (or spy) Agency. Of course, learning the standard terminology used in the field is also important.
Advanced skills you should learn include covert surveillance, and the basics of police interrogation (for when you're caught.) After learning these, you'll be on your way as the next James Bond in no time!

CIA Jobs
Getting hired at a spy agency is no easy task, though thousands of people do it each year.
Depending on the Intelligence Agencies available where you live, you might have an option to apply (such as with the CIA in the US and MI6 in the UK), or you may only get chosen if you meet certain skills deemed useful by the Agency.
Once you've applied, you'll be subjected to a battery of tests.
These could things as wide ranging as a polygraph to ensure you're not working for a rival Intelligence agency or harbouring negative thoughts about your government, and psychological assessments to determine your real motivation to work for the Agency.
Background checks to determine your personality and lifestyle, and to determine possible weaknesses. a credit check to ensure you don't have money woes, and reference checks on all the information you've provided are also common, as are several interviews.
Once all of this is completed, you just might be offered a job! Only a very small amount of people who apply to work for an Intelligence Agency ever get hired, and an even smaller amount of them work in clandestine or secret jobs.
The training spies go through is very rigorous, and can take many months or even years depending on the Agency.
Getting Hired
It can take up to a year and many background checks before you get hired at an Agency.

Intelligence Officer
Before you walk the walk, you have to talk the talk
Tradecraft
Most people probably haven't heard of the term "tradecraft" unless they've read books like those of John le Carré. Tradecraft is a blanket term that describes all the things used by a spy to commit espionage.
These skills include things such as covert photography, surveillance, secure communications and the "handling" of Intelligence Agents.
While certain skills such as hand to hand combat, computer hacking, and demolitions and explosives can be useful to a spy, they can't be used effectively by a spy without first learning the fundamentals of Intelligence gathering and the fundamentals of Espionage.
Secret Agents, Spies, and Intelligence Officer
One of the terms most misunderstood by amateurs in Intelligence and espionage is the term "spy."
Because of the proliferation of spy-fiction such as James Bond, and real-life TV shows such as Spooks in Britain, and movies such as The Recruit in the United States, the terms have taken on new meanings.
By definition Spy-Fi (spy fiction) uses the word "spy" to refer to the Intelligence Officer, the James Bond of the novel; this is the protaganist and the one using the gadgets and performing the stunts.
The term Secret Agent is also commonly used to refer to an Intelligence Officer in such a position. This may have developed in relation to "Special Agent", which is the term used in the United States to refer to several types of investigators.
When compared to the official use of these terms however, a different picture emerges. The term "spy" is used in official circles (if it's used at all) to refer to Intelligence Agents.
An Agent is separate from the Intelligence Officers that are employed by a service such as MI6 or the CIA. Instead, the Agent is the person giving information to the Officer.
In practice this means that the Agent often puts himself in much more danger than the Officer and very well can be called a spy, however he's not a member of the Service.
Of course, the fact that the term "Agency" is used to refer to various departments of the government (including the CIA -- the Central Intelligence Agency) complicates things further.
The simplest way to avoid this confusion is to use the official terms: Intelligence Officer to refer to an employee of an Intelligence Service, and Intelligence Agent (or simply Agent), to refer to the people the Officer recruits to give him information.
It's also helpful to define the term "espionage" and it's relation to Intelligence. Espionage is the act of gaining secret information. A person who engages in espionage is considered a spy.
A spy uses learned tradecraft while gathering this information. The information the spy gains is subjected to the Intelligence Cycle, which then produces valuable Intelligence. The Intelligence is then acted on by whoever requires it.
Terminology
Intelligence is information, collected by an Agent, given to an Officer, and run through the Intelligence Cycle.
The Spying Game

The Dead Drop
A dead drop is a location used by two people to communicate covertly. The idea behind a dead drop is that a spy can't be seen with his handlers (the people he's working with, his bosses) without compromising both who he is and what he wants with them.
In order to protect items that were left in areas where they could potentially be found (by squirrels or other animals in trees, by hunters or curious kids), various methods were invented to protect them. An example of this was the dead drop spike.
The spike looks like a thin stake or a thick pencil, and had an end that could be removed in order to add items; this spike would then be stuck in the ground where it would remain until the spy or his handlers retrieved it.
In the Internet Age, a new type of dead drop is emerging as well, the digital dead drop. Like their physical counterpart, digital dead drops aim to allow people to communicate in secret without exposing themselves
Dead Drop
The dead drop is used by an Agent and an Officer to communicate without having to meet face-to-face.

Covert Photography
Every spy at one point or another is going to need to know how to take photographs without being noticed. There are several methods of taking photographs without being noticed, depending on your situation.
If you're on foot, you've got several options. You could use a simple digital camera or you could use a more sophisticated approach. Cameras are available that fit into watches, pens, and even sunglasses!
If you'd like to get especially spy-like, there are cameras that fit into your button. All of these are surprisingly inexpensive, with the pen running for $99, the watch for $159.99, the sunglasses for $229.50, and the button cameras running from $119.50 up to $229.99.
If you're far away, a telephoto lens is extremely useful. This type of lens allows you to be "zoomed" in from extremely far away and still maintain the quality of clarity of the original image, as if you were standing there. These lenses can run the gamut from $200 all the way up to $10,000 should you be willing to spend the money.
Don't underestimate the power of satellite imagery either; using services such as Google Earth can help you during surveillance. This allows you to get a bird's-eye-view of the area, plan entry and exit routes for operations, and mark important buildings like Police and Government buildings that may pose a problem to your mission.
Secret Photography
Learning how to take photos and properly perform surveillance is essential tradecraft for any spy.

How to Disguise Yourself
The easiest part of any disguise is the clothing. A change of clothes (from a worker's outfit to a suit and tie for instance) can dramatically alter a person's appearance. In addition, the dying or cutting of hair, the use of contact lenses in the eyes, the growing of a mustache (time permitting), and the modification to teeth can all be used with dramatic effect.
Growing your hair longer than normal is normally helpful, as you can cut it if you need a snap disguise (see below.) In addition to contact lenses to change the colour of the eye, they can also be used to change the shape.
A mustache or beard can be used to conceal crucial parts of a person's face, and the use of iodine can very quickly stain someone's teeth yellow (for example, if you were acting like a homeless person for a disguise.)
Realize that fake mustaches, beards, and wigs are usually not advised. While people can pass wigs off as being realistic, the vast majority of false beards and moustaches look fake and will arouse suspicion.
You may also use a snap disguise, a one-off disguise that you come up with quickly. Snap disguises don't have to be physical modifications to yourself (such as the addition of a hat or a cane), but can in fact also involve your voice, your gait (the way you walk), or almost any other part of you.
The reason the snap disguise is useful is because you may be following a suspect and realize he suspects you're following him. While the golden rule of surveillance is not to freak out, if you know you're dealing with someone skilled in surveillance detection it can be helpful to change your appearance to blend into a crowd or disappear from his "radar."
Disguise Techniques
When disguising yourself, try to blend in with those around you, and keep their attention off your memorable features.
CCTV in Britain

Spying Software
If you're interested in spying on a computer system, there are a variety of software options that you can utilize. Keyloggers and RAT (Remote Access Trojans) can be used to monitor the keys typed in, or the entire activity of the computer. In addition, there exists software for hooking into specific programs such as Skype for spying on them.
While there's a variety of software that can be found on the Internet for various prices, they all come down to one of those two categories above (RAT or keylogger.) The software also has a variety of price points, from free up until several hundred dollars.
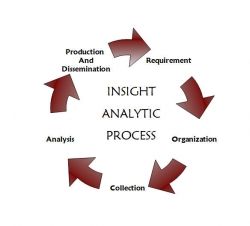
The Intelligence Cycle
From Information to Intelligence
Intelligence Officers and Agencies use a term called the Intelligence Cycle to describe a set of actions used to work through Intelligence.
The Intelligence Cycle is comprised of the following 4 or 5 actions:
1. Determine a need for Intelligence
2. Collect the Intelligence
3. Process the Intelligence (get it all together)
4. Analyze the Intelligence for It's value
5. Disseminate a Completed Report
Occasionally steps 3 and 4 are combined, depending on the Intelligence Agency. Every spy learns to follow these 5 steps to create Intelligence, or "actionable information" -- information you can use to make decisions. It is this information that the spy collects.
Intelligence Cycle
Even if you never explicitly use the Intelligence Cycle, you'll probably run through the steps while analyzing Intelligence anyway.
Spy Training Courses






How to Interrogate People
When you're captured, you have to know how a police officer is going to interrogate you. Police use four stages, which are detailed below:
Stage I. Calm you Down
Stage II. Establish a Rapport
Stage III. Theme Development
Stage IV. Elicit a Confession
Stage I is asking them basic facts and information to calm them down, because being in a police interrogation room can stress them out (and you're supposed to be controlling the stress.)
Stage II is to watch if they lie (watch their face for any subconscious eye movements, face-touching, etc. while you're asking them questions you know are true, and then questions you think they'll lie on.)
Determining a common ground is important here.
Stage III is taking advantage of the lies and suggesting an alternative "Theme development" is used. They pick something like, "It was an accident, right?" and they push it for a little.
If the accused is receptive, they continue on that track. If not, they switch to a new one until they find one that the accused will agree on.
Stage IV is after you've got that receptiveness, and now you pressure them to get the whole story. They're beginning to crack, and you keep the heat on, until the inevitable confession.
Police Interrogation
Interrogation is all about trickery. Hold your ground, and don't say anything.
Spy vs Spy
What's your opinion of spies in this modern day?



